Downloading a Key from AWS
When you create a new EC2 instance by using the wizard in AWS Management Console, a key pair is generated at the end of the EC2 instance creation process. A key pair consists of a private key and a public key. Secure Shell (SSH) is the encryption protocol, and the key pair is used to asymmetrically encrypt the connection. A public key can be generated by using the private key. When a key pair is generated for an Amazon EC2 instance, the public key is saved in the configuration of Linux installed on the EC2 instance, and the private key is downloaded by the user.
You must download the private key at the final step of the Amazon EC2 instance creation process and save the key in a safe place. The EC2 instance won’t be created until you download the private key. The private key is provided in a PEM file. Keep in mind that this is your only chance to download the key for the current AWS EC2 instance.
I download the private key and save the key as the blog01-key.pem file.
Connect to EC2 Instance via SSH Using PuTTY
PuTTY is a free SSH client that you can install on Windows. You must convert the downloaded PEM file to a PPK file format, which is supported by PuTTY, before you can connect to AWS via SSH. For this reason, you need to use the PuTTY Key Generator (PuTTYgen) utility, which is installed with PuTTY from a single installation file. You can also download puttygen.exe manually. PuTTYgen is used to generate RSA and DSA keys.
As a result, I have three files on the Windows machine from which I am going to connect to EC2 instances:
blog01-key.pem
putty.exe
puttygen.exe
These files are located in “C:\AWS SSH\” in this example.
Open PuTTY Key Generator (PuTTYgen) by clicking the puttygen.exe file or a shortcut to this file.
Click Load in the PuTTYgen window.
Click Select All Files (*.*) and browse the PEM file. We select “C:\AWS SSH\blog01-key.pem“. Then click Open.
Read the displayed notice and hit OK.
Now you can see the string of your public key in the window of PuTTYgen. Use the configuration as displayed on the screenshot below.
Type of key to generate: RSA
Number of bits in a generated key: 2048 bit
Click Save private key.
Are you sure you want to save this key without a passphrase to protect it?
Hit Yes if you agree. If you don’t agree, go back and protect the key with a passphrase.
Save the private key to a safe location. I save the key as “C:\AWS SSH\AWS EC2 SSH.ppk“. Hit Save.
How To SSH into EC2 Instance from Windows
Check the public IP address of your AWS EC2 instance. The instance must be in the running state to have a public IP address. In my case, the public IP address is 52.55.222.44. I will use this IP address for connecting to AWS via SSH.
Open PuTTY in Windows. Run putty.exe or the appropriate shortcut.
Go to SSH > Auth.
Click Browse and select the PPK file (the private key). I select the “C:\AWS SSH\AWS EC2 SSH.ppk” file generated in PuTTYgen earlier.
Go back to the Session screen in PuTTY and enter the public IP address of your EC2 instance in the Host Name (or IP address) field. Ensure that the connection type is SSH. I enter 52.55.222.44, which is the IP address of my EC2 instance copied from the EC2 Management Console. TCP port 22 is selected. Hit Open.
The security alert is displayed. Read the message and hit Accept to continue and connect to the EC2 instance. This dialog is displayed when you connect to a particular remote machine for the first time. The fingerprint displayed in the message must match the fingerprint of the EC2 instance.
Enter the user name in the console window. As I use Ubuntu Linux on my EC2 instance, I use ubuntu, which is the default user name configured for this instance deployed from the appropriate Amazon Machine Image (AMI).
Default user names for different types of Linux AMIs in AWS:
- Amazon Linux 2 or the Amazon Linux AMI: ec2-user
- CentOS: centos or ec2-user
- Debian: admin
- Fedora: fedora or ec2-user
- Red Hat Enterprise Linux (RHEL): ec2-user or root
- SUSE: ec2-user or root
- Ubuntu: ubuntu
- Oracle: ec2-user
- Bitnami: bitnami
Once you see the command prompt of a Linux shell (bash in this case), you can run commands on the remote Linux machine running in AWS. This means that you’ve set the proper AWS EC2 SSH configuration in PuTTY.
Transferring files via SSH to Amazon EC2 instances
I have configured remote AWS SSH access to the EC2 instance, and now I can connect to AWS instances via SSH, run commands, edit configuration, etc. However, you may also need to transfer files via SSH to AWS instances from your Windows machine or in the other direction. There are file transfer protocols that work over SSH to transfer files securely from one machine to another, for example, Secure File Transfer Protocol (SFTP) and Secure Copy Protocol (SCP).
To transfer files via SSH to AWS instances from Windows, you can use WinSCP, which is a free tool for Windows. Note that scp must be installed on the remote Linux machine running in AWS.
Once you have installed WinSCP on the Windows machine, run the application.
Select SFTP as the file protocol and, in the Host name field enter the public IP address of your EC2 instance to which you want to connect via SSH to transfer files. Enter a user name for your EC2 instance. I use 52.55.222.44 as the IP address and ubuntu as the user name in my example.
Click Advanced in the main window of WinSCP.
Go to SSH > Authentication in the Advanced Site Settings window. Click … in the Authentication parameters section and select the private key you previously generated in PuTTYgen. In my case, I select “C:\AWS SSH\AWS EC2 SSH.ppk“. Hit OK to save the settings and go back to the main window of WinSCP.
Click Login in the main window of WinSCP.
A warning message appears as it did when connecting to the EC2 instance from PuTTY for the first time. Hit Yes to continue.
If the AWS EC2 SSH configuration is correct, and you set the SSH connection parameters in WinSCP successfully, you can see the window with two panes in the commander style. The user folder of the local Windows machine is displayed in the left pane, and the user home folder of Linux running in AWS is displayed in the right pane. You can drag and drop files from one pane to another and copy, rename, or delete files on the local and remote machines.
Connecting to AWS via SSH from Linux
Unlike Windows, Linux has a native SSH client. In the console of your local Linux machine, use the command like the following for connecting to AWS EC2 instances running Linux via SSH:
ssh -i file_name.pem ubuntu@ip_address
Go to the directory where your private key .pem file is located on a Linux machine. In this example, I use Ubuntu, and I downloaded the blog01-key.pem file to ~/Downloads/.
cd ~/Downloads/
ssh -i blog01-key.pem ubuntu@52.55.222.44
Where ubuntu is the user name on the remote Linux machine, and 52.55.222.44 is the IP address of the remote Linux machine.
If you run this command now, you would get the error:
Warning: Unprotected private key file.
Permissions for ‘blog01-key.pem’ are too open.
It is required that your private key is not accessible by others.
This private key will be ignored. Load key: pad permission.
Permission denied (publickey).
You need to set lower (stricter) permissions for security reasons.
chmod 400 ./blog-key.pem
Use 400 if the keys must be only readable by you.
Use 600 if you need the keys to be readable and writable by you.
Now you can connect to AWS EC2 instances via SSH from your Linux machine with the command:
ssh -i blog01-key.pem ubuntu@52.55.222.44
Now I am connected via SSH to an Amazon EC2 instance.
Transferring files via SSH to Amazon EC2 in Linux
You can also transfer files via SSH to AWS instances by using SCP in Linux. Make sure you have already established an AWS SSH connection to the remote Linux instance from your local Linux machine. Then, open a new console on your local Linux machine and connect to the EC2 instance by using the command like:
scp -i /path/key_name.pem /path/file_name.txt user_name@ec2_instance_IP_address:/path_to_file
In my example, I use the command:
scp -i ~/Downloads/blog01-key.pem ~/Downloads/file.txt ubuntu@52.55.222.44:/home/ubuntu
Transferring files via SSH to the AWS instance has been completed successfully.
In order to copy a file in the reverse direction (from Linux in AWS EC2 to your local Linux machine), use the command like:
scp -i /path/key_name.pem user_name@ec2_instance_IP_address:/path_to_file/my-file.txt path/my-file2.txt
In my case, I use the command:
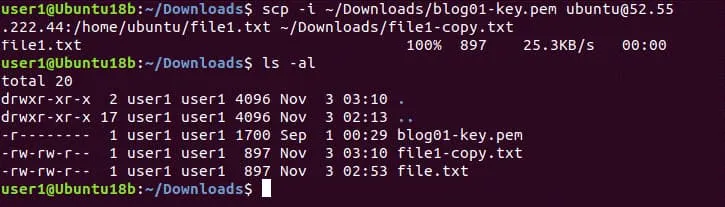
scp -i ~/Downloads/blog01-key.pem ubuntu@52.55.222.44:/home/ubuntu/file1.txt ~/Downloads/file1-copy.txt
As you see in the screenshot, the file has been copied successfully. You can copy important files from an Amazon EC2 instance to the needed local computer and back up the files. Perform AWS EC2 backup regularly to avoid data loss.
How to Add a New Key to an AWS Instance
You can create an additional key pair for an existing EC2 instance for connecting to AWS instances via SSH after you create the AWS EC2 instance. You may need to do this for providing SSH access to the EC2 instance for other users. When you think that the user doesn’t need to connect via SSH into AWS instances, you can delete the public key from the Linux machine running in AWS EC2 without the need to recreate a new key instead of the key generated at the moment of instance creation.
Open EC2 Management Console in AWS Management Console.
Go to Network & Security in the navigation pane and click Key Pairs.
All existing key pairs are displayed on this page. You can type a part of an existing key pair name in the search field to find the key pair.
Click the Create key pair button in the top right corner of the web interface to create a new key pair for an existing EC2 instance.
Select .pem as the private key format if you need to use a key in Linux with OpenSSH or select .ppk if you need to use the key in Windows with PuTTY. As I’m going to use a local Linux machine for connecting to AWS EC2 instances via SSH with a new key, I select the .pem key option. You can add tags if needed. Hit Create key pair when ready to continue.
Save the downloaded file in a safe place. In my case, the name of the downloaded file is blog02-temp.pem and I save this file to the Downloads directory in the home user directory.
Retrieving a public key from the new key pair
We have generated a new key pair in the web interface of AWS Management Console. Now we need to generate a public key by using a private key from the downloaded .pem file.
Use the command of this format:
ssh-keygen -y -f /path_to_key_pair/my-key-pair.pem
In my case, the command is:
ssh-keygen -y -f ~/Downloads/blog02-temp.pem
If you get an error, set the correct permissions:
chmod 400 ~/Downloads/blog02-temp.pem
If everything is correct, a generated public key is displayed in the console output.
Copy the generated key string and save this information in a safe place. In this example, I save the key string to a text file.
Copy the key string to the clipboard.
Connect to EC2 instances via SSH from your local Linux machine as explained above in this post.
We are located in /home/Ubuntu/ now.
Open the configuration file where public keys to access the EC2 instance via SSH are stored with a text editor:
nano ~/.ssh/authorized_keys
The full path to this configuration file depends on the Linux Amazon Machine Image (AMI) and can be:
/home/ubuntu/.ssh/authorized_keys
/home/ec2-user/.ssh/authorized_keys
/root/.ssh/authorized_keys
Paste your key from the clipboard to the second line in this configuration file.
Save changes and close the file.
Don’t close the console (terminal) with the current SSH session that you use for connection to the EC2 instance until you ensure that the second key you have added works. Otherwise, you can lose SSH connection if the configuration is incorrect without the ability to connect to AWS instances via SSH. Don’t lock yourself out in case of a mistake!
Open another terminal on your local Linux machine and try to connect to the instance by using a new key. I go to the directory where my .pem key files are located.
cd ~/Downloads/
Connect to the EC2 instance running Linux in AWS from your local Linux machine in the new console by defining the new private key (blog02-temp.pem in this case).
ssh -i blog02-temp.pem ubuntu@52.55.222.44
AWS SSH connection has been established successfully with the new key. Now you can send the new key (blog02-temp.pem) to a user who needs to establish the AWS SSH connection. When you will need to disable SSH access to this AWS EC2 instance for the user, delete the second line from .ssh/authorized_keys on your remote Linux instance running in AWS EC2. Since the AWS SSH configuration with both keys (the first key that was generated when you created the EC2 instance and the second key you created before for another user to connect to AWS EC2) works fine, you can close the SSH terminal windows.
If you delete a key pair in Network & Security > Key pairs from the EC2 Management Console (the place where we created the second key in the web interface of AWS Management Console), keys inside the particular EC2 instance are not deleted.
What to Do if You Lose the AWS EC2 SSH Key
If you lose the private key for connecting to an AWS EC2 instance (that was generated when creating a new EC2 instance), you can no longer connect to the appropriate instance. You cannot generate a new key and insert the new key to the AWS SSH configuration file in the current EC2 instance. In this situation, you can use a temporary EC2 instance to which you have SSH access. Try the following workflow to restore AWS EC2 SSH access to the instance.
- Stop the original EC2 instance, the AWS SSH private key to which you have lost.
- Check information about EBS volumes attached to the EC2 instance. You need to identify the EBS volume that contains the root / volume mounted to Linux. Note the volume ID of this EBS volume.
- Launch a temporary instance in AWS EC2. You can use the instance running the same Linux distribution as installed on the original machine (the AMI of the same type).
- Generate a new key pair connecting to AWS in AWS Management Console. Save the private key and prepare the public key. You need to generate the key string of the public key to repair the AWS SSH configuration stored on the root volume used by the original instance.
- Create a directory in Linux running on the temporary EC2 instance and mount the EBS volume that contains the root / partition of the original EC2 instance to the temporary EC2 instance. Locate the needed EBS volume by the volume ID you noticed before.
- Open the AWS SSH key configuration file (that was located in a directory like /home/Ubuntu/.ssh/authorized_keys). The path is changed depending on the directory to which you mounted the root partition of the original EC2 instance. Add the key string of the new public key to the AWS SSH key configuration file.
- Unmount the EBS volume used by the original EC2 instance that is attached to the temporary EC2 instance.
- Mount the EBS volume that contains the edited AWS SSH key configuration file back to the original EC2 instance.
- Power on the original EC2 instance and connect to this instance by using a new key pair via SSH.
Using EC2 Instance Connect
Key management is an important part of AWS administration because you need to keep AWS EC2 SSH keys for accessing EC2 instances in a safe place and also prevent losing them. Creating and deleting keys needed for temporary access of other users can be a routine task with a large number of users. For this reason, Amazon provides the ability to connect to AWS EC2 instances via SSH by using EC2 Instance Connect. This feature allows you to automate SSH key management for connecting to AWS instances.
The idea of using EC2 Instance Connect is that you create Identity & Access Management (IAM) policies to control AWS SSH access to EC2 instances centrally without the need to manage (create, share, delete) SSH keys manually. Finally, users can use an SSH client, a browser-based client of AWS EC2 console, or Amazon EC2 Instance Connect CLI for connecting to AWS EC2 instances.
The Amazon Instance Connect API pushes a one-time-use public SSH key to the instance metadata for 60 seconds. The IAM policy associated with the IAM user authorizes the user. The user must connect to the EC2 instance by using this key within 60 seconds. After the key expires, a new key must be used.
Amazon Instance Connect is supported for EC2 instances on which Ubuntu 16 (or higher) and Amazon Linux 2 are installed. Amazon Instance Connect must be installed on the EC2 Linux instance. Another prerequisite is the installation of AWS CLI on the remote Linux machine running in AWS.
After installation, EC2 Instance Connect executes the script that writes data to these parameters in the configuration file (/etc/ssh/sshd_config) of the SSH server daemon:
AuthorizedKeysCommand
AuthorizedKeysCommandUser
The updated AuthorizedKeysCommand configuration is used to read public AWS EC2 SSH keys from EC2 instance metadata. If custom values have been already entered for these parameters, Instance Connect doesn’t update (overwrite) them, but you cannot use the feature in this case.
You need to create a configuration file in JSON format. Open IAM Console, then go to Policies and hit Create Policy. As an alternative, you can use the command-line interface on your Linux machine with AWS CLI installed. The configuration example is displayed below. This policy can identify instances by the instance ID to allow access.
{
“Version”: “2021-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Action”: “ec2-instance-connect:SendSSHPublicKey”,
“Resource”: [
“arn:aws:ec2:region:account-id:instance/i-00000000000000000”,
“arn:aws:ec2:region:account-id:instance/i-00000000000000001”
],
“Condition”: {
“StringEquals”: {
“ec2:osuser”: “ami-username”
}
}
},
{
“Effect”: “Allow”,
“Action”: “ec2:DescribeInstances”,
“Resource”: “*”
}
]
}
Then the policy must be activated. The AWS CLI command to activate the policy will look something like this:
aws iam create-policy –policy-name my-policy –policy-document file://JSON-file-name
You can attach the activated policy to the appropriate user.
aws iam attach-user-policy –policy-arn arn:aws:iam::account-id:policy/my-policy –user-name IAM-friendly-name
In order to connect to the EC2 instance in Amazon EC2 Console, select the needed EC2 instance, and hit the Connect button. On the Connect to instance page, select the EC2 Instance Connect tab and hit Connect.
Conclusion
Connecting to AWS EC2 instances via SSH is an important part of the AWS EC2 administration process. This blog post explained how to make an AWS EC2 SSH configuration and connect to AWS EC2 instances running Linux from local Linux and Windows machines. Key pairs must be used to establish the SSH connection with EC2 instances. A public key is stored in the configuration of Linux running in AWS EC2 and a private key is used by a local SSH client installed on a user’s machine. Keep keys in a safe place and make backups regularly to avoid losing data, time, and costs.






























No comments:
Post a Comment